Infrastructure-as-Code: 3 Pipeline Scenarios for Continuous Integration & Delivery

Infrastructure-as-code (IaC) takes all of the proven techniques of DevOps software development and applies them to cloud infrastructure. It’s a type of configuration management that can codify an entire organization’s infrastructure resources, committing them to a control system to enable more effective workflows.
It’s not uncommon for cloud applications to have separate deployment environments for the different stages of their release cycle. Development, staging, and production environments are often used as separate entities, composed of networked resources such as databases and application servers. Occasionally these environments fall out of sync, and this “environment drift” can have a devastating impact on development. IaC is an antidote to this problem, allowing app development teams to use Continuous Integration (CI) and Continuous Delivery (CD) pipelines to achieve the following seamlessly:
- Decrease lead times for changes and features
- Increase in deployment frequency
- Decrease in change failure rates
- Stronger feedback loops
- Improved code quality and security
The above improvements lead to a marked increase in productivity and product quality, which has a noticeable impact on customer satisfaction. However, delivering IaC to multiple or hybrid environments is a challenge that many organizations have yet to conquer. It’s incredibly complex and riddled with security and compliance issues that require a great deal of forethought and planning.
Overcoming Obstacles to Infrastructure-as-Code
There’s no doubt that IaC is a valuable methodology for operations teams, but it can present its own challenges. Tracking can be an issue. Namely, the ability to check the divergence of actual infrastructure from the committed infrastructure code, and alerting the team when it happens. Another challenge is perfecting the ability to orchestrate complex code automation in order to capitalize on the true potential of IaC.
Overcoming the Obstacles
Laying pipelines for IaC provides a match-ready orchestration and execution medium in which to roll out infrastructure changes, very similar to that of application code. These pipelines for infrastructure can be used in the following scenarios:
1. Building Immutable VM Images for Cloud Platforms
In order to stay on top of compliance, security, and performance, organizations often build custom virtual machine (VM) images to host their platforms. It’s a good idea, but building those images via pipelines ensures consistency and execution tracking can solve many problems:
 Example Tools: Packer, Vagrant, Linuxkit
Example Tools: Packer, Vagrant, Linuxkit
2. Applying Infrastructure Changes
Infrastructure changes are critical tasks and should be carried out with caution. One small change to infrastructure can have a cascading effect, so it’s vitally important that the code goes through a rigorous verification process. Using an auditable pipeline helps in the execution of orchestration of such changes, and also gives teams greater confidence and peace of mind:
Simple Pipeline for Infrastructure-as-Code
Complex Pipeline for Infstrastructure-as-Code
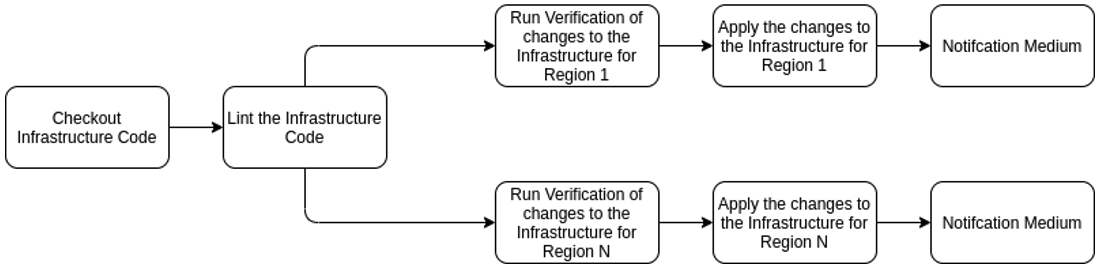 Example Tools: Terraform, CloudFormation
Example Tools: Terraform, CloudFormation
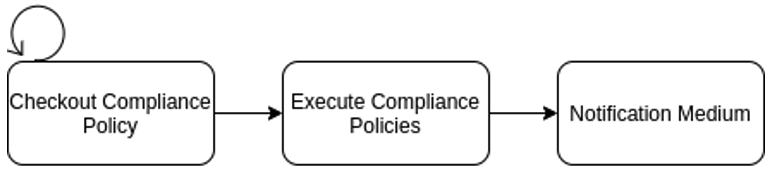
3. IaC Pipeline and Drift Detection
For highly-regulated industries like healthcare and finance, compliance with government and industry standards is a day-to-day issue. Some of these standards require periodic validation of computing and network infrastructure. Executing these checks using pipelines provides a layer of transparency and drift detection that would otherwise be impossible to attain:
Compliance-as-Code Pipeline
Drift Detection
Example Tools: Inspec, Prowler
The Road Ahead
Cloud-native components have boomed in popularity in recent years, giving rise to GitOps continuous delivery patterns. GitOps empowers developers to perform tasks that would otherwise fall to the feet of IT operators. Declarative descriptions of infrastructure changes are stored in a Git repository, which can then be automatically matched to the infrastructure state, giving teams unparalleled visibility.
Core GitOps principles include the following:
- The entire system infrastructure is described declaratively
- The desired system state is versioned in Git
- A mechanism to ensure correctness and alerts on divergence
- Changes to infrastructure are raised via PR. Approved PR changes are automatically applied to infrastructure
To learn more about IaC pipelines and how Apexon can help your organization streamline its development processes, simply get in touch using the form below.