ISO 27001 and AWS Compliance Is A Risk Management Priority

As the global village that we all live in continues to be ever more hyper-connected and digitized, the need to keep critical information safe and secure becomes a business optimization priority. And while cybersecurity is often taken for granted by end users, the threat of malicious actors gaining access to data and systems can be a constant headache for digital decision makers.
The list of companies or brands that have a cyber-attack on their corporate resume is hardly exclusive. In fact, it is harder trying to find an organization that has not had an issue with cybersecurity and there is a consensus that increased (and necessary) digitization will continue to flag up why digital risk management is a priority.
Naturally, protecting digital assets using an effective cyberinfrastructure is a given in the age of constant and more sophisticated cyber threats. What matters is that companies need to feel confident that their defenses are not only secure but scalable enough to deal with anything that black-hatted hackers can throw at them.
The recent ransomware attacks by the REvil group, for example, might not have ensnared major names (to date), but its focus on the “supply chain” of managed services, according to the BBC, shows that cyber-criminals are often ahead of the game when it comes to finding exploitable holes. For that reason alone, companies must make certain that they have as much digital security as possible.
One of the protective shields of cyber data is the international information security standard ISO 27001. An Information Security Management System (ISMS) that is well-structured and developed in compliance with accepted international standards is an ideal foundation for comprehensive security and optimum achievement of business objectives.
With that in mind, let us take a deeper dive into this standard and see how it can become part of your risk management processes.
What is ISO 27001?
ISO 27001 is a universal standard for risk management specifically designed to protect information.
Based on the ISO 27002 best practice guidelines, ISO 27001 is widely known to specify security management best practices and security controls in a comprehensive manner. As a result, ISO the standard is an excellent guide for the selection of proportionate and adequate security controls to protect said information.
In addition, the domains included in ISO 27001 are designed to leverage an improved ISMS model that is comprehensive in its overall management, ranging from establishing, operating, implementing, monitoring, maintaining, reviewing and improving the security of defined digital assets.
ISO 27001: Needs & Requirements
For companies that want to improve their ISMS, ISO 27001 should be both a key benchmark and an acknowledgement that the company aspires to commit to an international standard of information security and mitigation of risks.
With that in mind, ISO 27001 is needed to achieve the following security objectives:
- Outline a comprehensive framework of information security management objectives
- Provide a secure framework for the implementation and management of security controls in an ideal manner
- Identify the potential security risks involved in business operations and information
- Manage the security framework in compliance with the business laws and regulations
- Underline the information security standards, policies, and processes followed by the business
The following list of ISO 27001 Security Domains shows where decision makers and IT managers should be looking to improve existing security protocols and patch any potential vulnerabilities:
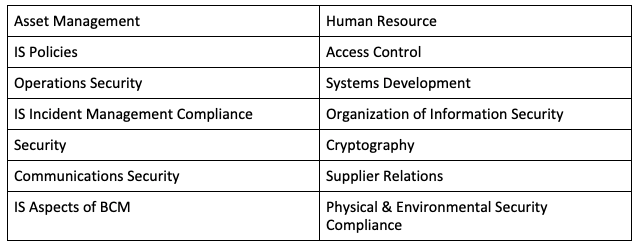
For context, ISO 27001 has 114 specific controls organized around 35 control objectives to protect information assets lying under the 14 security domains above.
However, as the implementation of ISO 27001 is a complex and time-consuming task, there is a defined trend for companies to use cloud service providers like AWS (Amazon Web Services) to cater to their IT infrastructure needs. For many of these companies, a third-party with a reputation for making security a priority is not a worthwhile investment but also an acknowledgement that taking security off-site is the way forward.
AWS and its Shared Security Model
AWS is the world’s leading cloud platform, offering over 200 fully-featured services used by the world’s fastest-growing start-ups, business enterprises and leading government agencies. In fact, the comprehensive cloud infrastructure of AWS is a critical part of lowering costs and operational expenses, becoming more agile and innovating faster
As you would expect from the Amazon empire, AWS’ strength is directly related to its size with the platform able to offer a global network of 81 Availability Zones within 25 geographic regions. And underlying that network is the concept that security and compliance is a shared responsibility.
The AWS shared security model is based on the fact that the relationship between AWS and its customers is understood from day one.
While AWS ensures the security of the cloud, its customers must take care of security in the cloud. Hence, AWS looks after the control and management of the host operating system, physical security of facilities, and virtualization layer. At the same time, customers must look after the management and configuration of security controls in the guest operating system and data encryption in transit and at rest.
This seemingly simple arrangement thereby helps to relieve operational burden for the customer and allows companies to shift management of certain processes to AWS, while maintaining control of their security environment.
Staying compliant with shared security
The caveat is that the implementation of ISO 27001 in a shared security model comes with novel challenges. In other words, while AWS provides advanced Identity and Access Management (IAM) services, customers are responsible for mapping appropriate access control policies and configuration of AWS Security Groups. This is where a company such as Apexon can be a valuable partner.
For organizations to stay ahead of cybercriminals, information security must be ever-evolving and in compliance with the relevant policies and standards and laws and regulations. AWS fulfills the standard requirements of high-end information security and is a certified ISO 27001 cloud platform.
AWS not only supports ISO 27001 but supports more security standards and compliance certifications than any other offering, including PCI-DSS, HIPAA/HITECH, FedRAMP, GDPR (General Data Protection Regulation), FIPS 140-2 and NIST 800-171. This dedication to security helps customers satisfy compliance requirements for virtually every regulatory agency around the globe.
Apexon is also ISO 27001 certified and follows best practices. Additionally, Apexon is an AWS advanced consulting partner. This means that we have a significant amount of experience in both working with AWS to provide the best possible security and compliance advice for our customers and internal knowledge as to how to protect data from unwanted attention. To put it into simple terms, we know not only where the holes could be but also where the criminals are looking.
As we are all aware, the digitalization of society is not going to slow down. That will mean that cyber-crooks are going to get more sophisticated and more innovative with every hack.
What matters is that we strive to stay ahead of those with nefarious goals, using white hat principles to be just as innovative and more secure. If you do not leave a door open, then it is difficult to get inside a physical building, and the same applies in the digital space. Provided you have the right security and compliance locks in place, then they can keep banging on the virtual door until they get bored and look somewhere else.
To learn how Apexon can help you with your compliance requirements, contact Apexon using the form below.
To learn more about AWS compliance offerings, please visit this link.