
Security Testing for Wearables: Protecting Your Data on Your Wrist

Wearable technology has seamlessly integrated into our daily lives, offering convenience and functionality. From smartwatches streamlining daily tasks to fitness trackers methodically monitoring our health, wearables have become an extension of ourselves. However, amidst this convenience lies a pressing concern – the security of our personal data. Wearables often collect a vast amount of sensitive information, including health metrics, sleep patterns, location data, and even financial details for contactless payments. A recent study by CFO Magazine reveals that 75% of professionals have witnessed a surge in cyberattacks over the past year.
How can we ensure that the convenience of wearables does not compromise the privacy and security of our sensitive information?
Also Read: From Traditional to Digital: Enhancing Payment Systems
To address this concern and ensure the safety of our data, it’s crucial to explore the security testing for wearables. In this blog post, we’ll delve into how security testing plays a crucial role in safeguarding your data on your wrist.
Security Vulnerabilities in Wearables
Wearables store vast personal data, making them attractive targets for cybercriminals. Health data, location history, and personal information are just a few examples of the sensitive data that wearables collect and transmit. With over 10.54 million IoT attacks reported in December 2022 alone, it’s clear that interconnected devices are increasingly targeted. A security breach could result in identity theft, unauthorized access to private information, and other consequences.
Some commonly identified security weaknesses in wearables are:
- Insecure communication: Data travels between your wearable, phone, or the cloud. Hackers can intercept this data if it’s not encrypted.
- Weak passwords & outdated software: Hackers can easily crack weak passwords and outdated software with known vulnerabilities.
- Physical security gaps: A lost or stolen wearable can expose your data without features like remote wipes or strong physical security measures.
Also Read: How Remote Patient Monitoring Works in 5 Steps
The Importance of Security Testing
Security testing checks for vulnerabilities and weaknesses in a system’s defences to protect against cyber threats. Proactive security testing is essential throughout the development lifecycle of wearable devices. By identifying and addressing vulnerabilities early on, manufacturers can enhance the security posture of their products and protect users’ data.
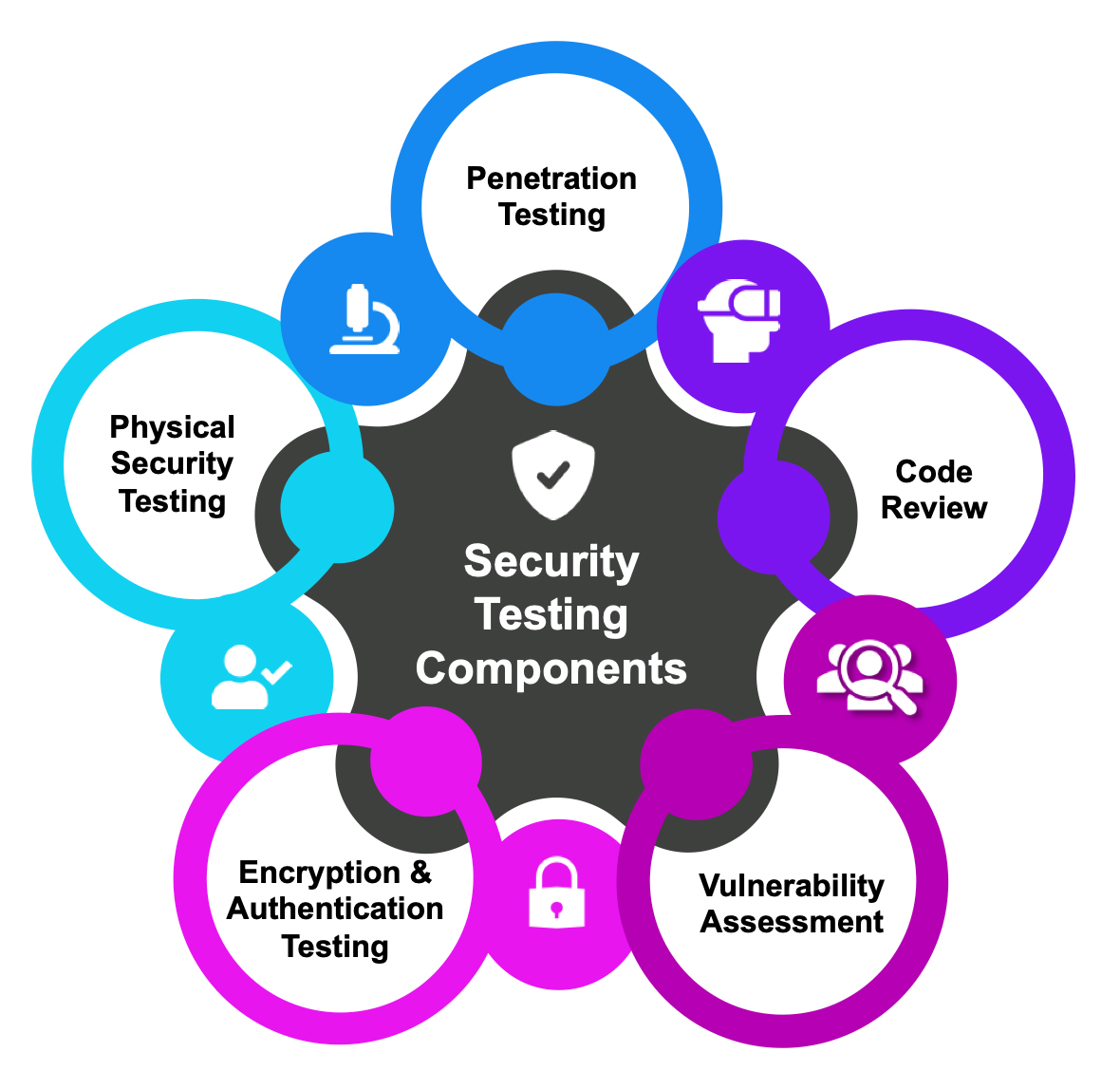
Key Components of Security Testing for Wearables
Also Read: 3 Ways Digital Twins Improve the Lives of Healthcare Payers
1. Penetration Testing:
Penetration testing, often called “pen testing,” involves simulating real-world attacks on a wearable device to identify vulnerabilities and weaknesses in its security defences. This process involves a skilled, ethical hacker attempting to exploit known vulnerabilities or weaknesses in the device’s hardware, software, or network infrastructure.
By conducting penetration tests, manufacturers can discover and address potential security flaws before malicious actors exploit them.
2. Vulnerability Assessment:
A vulnerability assessment systematically examines a wearable device’s hardware and software components to identify potential security vulnerabilities. This process involves automated scanning tools to detect known vulnerabilities in the device’s firmware, operating system, and applications. Manual analysis can be conducted to identify less apparent vulnerabilities that automated tools might miss.
A vulnerability assessment aims to provide insights into potential weaknesses that attackers could exploit.
3. Code Review:
Code review is a critical component of security testing for wearables. It involves a thorough examination of the device’s firmware and software code. This process is typically performed by skilled software engineers or security experts who analyse the code for security flaws, adherence to coding best practices, and potential vulnerabilities.
Code review helps ensure that the wearable device is built using secure coding practices and that any vulnerabilities or weaknesses are identified and addressed before the device is deployed to users.
Also Read: Integration of Wearable Devices with EHR
4. Encryption and Authentication Testing:
Encryption and authentication are fundamental security measures for protecting data transmitted and stored by wearable devices. Encryption testing confirms the effectiveness of encryption algorithms, safeguarding sensitive information from unauthorized Authentication testing assesses the strength of authentication mechanisms like passwords or biometrics, ensuring robust protection against unauthorized entry.
Manufacturers can ensure that user data remains secure and protected from unauthorized access by testing encryption and authentication mechanisms.
5. Physical Security Testing:
Physical security testing assesses the measures to protect wearable devices from physical tampering, theft, or unauthorized access. This includes evaluating device enclosures’ robustness, anti-tamper mechanisms’ effectiveness, and the security of communication ports and interfaces. Physical security testing helps ensure that wearable devices remain secure even when physically accessible to attackers.
By implementing adequate physical security measures, manufacturers can mitigate the risk of unauthorized access to sensitive data stored on wearable devices.
Also Read: Wearables Testing: An Emerging Practice Under Construction
Best Practices for Wearable Security
Users can take proactive steps to enhance the security of their wearable devices:
– Keep firmware/software updated.
– Use strong, unique passwords and enable two-factor authentication.
– Exercise caution when granting permissions to third-party apps.
– Avoid connecting to unsecured Wi-Fi networks.
Conclusion
As wearables become more sophisticated, so must our approach to security. Manufacturers need to prioritize ongoing testing and user education. Users, in turn, must be aware of the risks and take proactive measures to safeguard their data.
Security testing is paramount in ensuring wearables’ safe and secure integration into everyday life. By understanding risks, adhering to best practices, and fostering collaboration between manufacturers and users, we can confidently navigate the digital landscape, ensuring the sanctity of our data and preserving privacy in an increasingly interconnected world.
Stay informed, stay vigilant, and safeguard your data—on your wrist.




