Why It’s Time to Think Seriously About DevSecOps

As the evolution of the software development lifecycle continues to pick up pace, there is an increasing need for companies to structure its DevOps functions to fit the pressing needs of the moment. With the pressure on developers to make certain that digital requirements are not only delivered on time but also robust enough to withstand the demands and challenges of the connected society, the shift towards a working process that allows companies to deploy products quickly and with minimal disruption is critical.
When you consider that global IT spending will total around $4.5 billion in 2022 (according to Gartner), then it becomes crystal clear that any investment into digital solutions that will accommodate the required business optimization strategies must be aligned to the software development lifecycle itself. For most companies, these strategies have always fallen under the watchful eye of the DevOps teams, but there is a consensus among developers and digital engineers that one of the most essential elements – Security – needs to be part of the puzzle from day one.
Taking the above into account, this blog post will take a deeper dive into how DevSecOps delivers what is required in the software release pipeline and why security matters across the entire SDLC.
What is DevSecOps?
A combination of three words (development, security and operations), the term DevSecOps has been part of the software lexicon for some time.
DevOps was always a team-centered culture that encompassed the attitude and behavior of a particular social group. In recent years there has been a noticeable shift from a pure DevOps attitude – one that was focused on solely on development and operations teams – to one that takes advantage of the agility and responsiveness of said teams by including security. For example, DevSecOps is built on the understanding that everyone in the SDLC is responsible for security, implementing best practices in every part of the development procedure.
DevOps was designed to encompass five key components; an Agile framework, build-once-run-anywhere development, everything-as-code, automation and communication/collaboration. If done well, this leads to faster deployment times, fewer failures and (in theory) quicker recoveries.
The caveat is that this agility does not seem to consider the need for security. Which, when you think about the constant attacks by malicious actors on digital infrastructure and our connected lives makes little sense.
On every level, this is an evolution that is not only necessary for successful deployment but also emphasizes the importance of security in the digital world that we all inhabit. If we think about how companies have been increasingly focused on digital transformation in recent years, then it follows that all aspects of the product lifecycle must take advantage of the tools that are available – in other words, DevSecOps.
And while there is a danger that both DevOps and DevSecOps can sometimes be viewed negatively – one recent industry report referred to the former as a “meaningless buzzword” – most people see value in having these aspects align. That becomes even more apparent when you factor in that the growing awareness of the latter will generate a market of more than $17 billion by 2028 – a compound annual growth rate of 24.1% from 2021 onwards, according to Grand View Research.
Why DevSecOps Matters
Traditional IT departments are fragmented, with Development, Security, and Operations all having different leadership and reporting structures. DevSecOps builds on the idea that cross-functional teams must work together and that everyone is responsible for security.
Process experts and coaches often say that DevOps is not about tooling. In some cases, there is a growing acceptance that a culture change is necessary for organizations of all sizes to sustain ongoing process improvement. When you think about what the term actually means, then it seems to be a no-brainer that anything that can bring ongoing quality and stability of information to computing systems should be part of the conversation.
In fact, executive stakeholders measure outcomes and results when making investments in process improvement. In our experience, for companies to achieve the goal of DevOps, quality software must be developed and deployed faster. For that reason alone, the “automate everything” mantra of the DevOps movement is central to DevSecOps as well.
The role of security in a software development of app lifecycle has traditionally been allocated to an isolated team, but those days are reportedly over. DevOps has always been about collaboration, but security – as we noted above – must be a shared responsibility. This mindset is crucial for the success of any digital product or service, even more so when you add the increased migration to cloud-based solutions.
With that in mind, there are workflow processes that can be followed to maintain security throughout the SDLC – a move towards Shift-Left concepts in the life cycle itself. For the purposes of this blog post, we are using the AWS Cloud to demonstrate this workflow.
The visual below shows how this can be achieved:
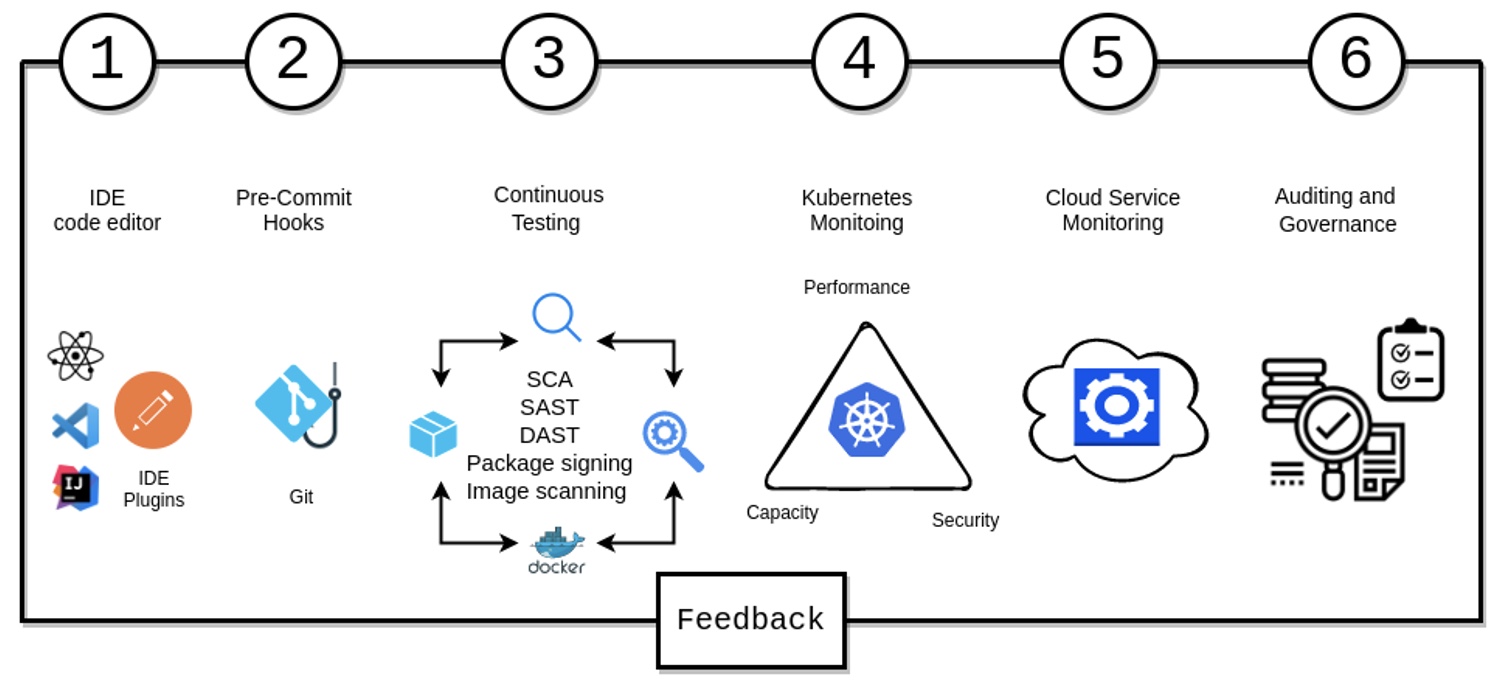
Each of these stages during the implantation and feedback loop can be further broken down as follows:
- IDE (Integrated Development Environment) – IDE Plugins perform security checks during the development itself, hence preventing the security bugs in code in early stages of development
- Pre-commit hooks – To ensure that the engineering team doesn’t accidentally commit the Secrets, Secret file or any other Sensitive Authentication Data, GIT hook should be incorporated before said engineering team pushes the changes to repository
- Continuous Testing
- SCA (Software Composite Analysis) – Detect publicly disclosed vulnerabilities contained within a project’s dependencies.
- SAST (Static Application Security Testing) – Catches bugs and vulnerabilities in application code using Static Analysis Code rules
- DAST (Dynamic Application Security Testing) – Helps you automatically find security vulnerabilities in your web applications while you’re developing and testing your applications.
- Artifact Package signing – Binary Artifacts generated from the Continuous Integration should be signed, to prevent of tampering of Artifact after being published. Signing of Artifacts can vary for different packaging formats and languages
- Container Image scanning, threat detections, SAST of containers. This is the process of analyzing the contents and the build process of a container image in order to detect security issues, vulnerabilities or bad practices
- Continuous Monitoring and Logging – helps the organization have an eagle’s eye view of their applications, deployments, infrastructure, and users, which allows them to get the required information quickly. In other words, monitoring and logging throughout the application lifecycle from development through production. This sets you up to deliver applications that are secure, stable, and high performance, using the following:
- AWS CloudWatch Logs, AWS CloudWatch Events (AWS Services)
- Prometheus, Grafana, ELK, Alert-manager (Open-source tools)
- Auditing and Governance – Process is about ensuring security and accountability for those that handle sensitive systems. Authorized stakeholders responsible for governance, risk management, audit, and compliance review build artifacts prior to approving a software release for deployment. Tools used here include:
- AWS CloudTrail
- AWS Identity and Access management
- AWS Config
How do we Measure DevSecOps Success?
The simple answer to this question is that we need to look at the KPIs and see where DevSecOps has been of value.
For example, has the deployment frequency (fast and frequent releases) been maintained? Is the lead time (the code to cash cycle) on track? Has the detection of threats, vulnerabilities and malware been effective? What is the mean time from repair to remediation? And, importantly, how efficient has the rollback and recovery been?
All of these KPIs are an essential part of measuring the success of a DevSecOps integration, but the benefits are often not limited to speed and security. Rather, the purpose and intent of this collaborative strategy is to (in the words of Shannon Leitz, co-author of the DevSecOps Manifesto), “build on the mindset that everyone is responsible for security with the goal of safely distributing security decisions at speed and scale to those who hold the highest level of context without sacrificing the safety required.”
The theory is that by delivering better and more-secure code faster, the SDLC becomes cheaper.
Research has shown that when software is developed in a non-DevSecOps culture, the inherent security problems can generate insurmountable time delays. Fixing these issues can often be even more time-consuming and expensive.
Integrating security requirements from the beginning reduces the chances of a product launch being delayed or (even worse) subject to unnecessary rebuilds. In addition, a proactive attitude to security can be extremely helpful in establishing a culture of quality at an organization.
DevSecOps: More than a Talking Point
The principles and practices of DevOps have been set in stone for a number of years, but the increased adoption of and migration to the cloud have brought security to the forefront of discussions. Ask any business leader what are the main concerns that they have with a potential cloud adoption and it is highly likely that they will be looking for a solution that is secure and, importantly, the right fit for their company.
A recent blog post by The Enterprisers Project highlighted 11 questions that decision makers should be asking about DevSecOps, with the consensus being that security is often an afterthought in the application development lifecycle. With so many malicious online actors making every effort to obtain unauthorized digital access to important data daily, the need for a secure product or ecosystem is no longer a talking point, but a defined business optimization strategy.
Enforcing security should be a consideration for all stakeholders, which makes the evolution of DevOps into a working practice that encompasses this requirement an important consideration. Ultimately, a culture of quality requires traceable and continuous insights to be successful, and adopting a DevSecOps model should be at the top of the list.
Apexon’s DevSecOps model is powered by a prototype-to-production process that covers Agile development practice, security, 100% automation and operational practices. To learn more about how our digital engineers can solve your toughest cloud enablement challenges, contact us by filling out the form below.